虚拟机 #
本文档主要介绍如何将istio安装到虚拟机中。
安装 #
生成安装包 #
# network 要与集群的network 保持一致
# 可使用下面的命令获取
export NETWORK=$(kubectl get ns istio-system -o yaml|grep topology.istio.io/network:|awk 'NR==1'|awk '{split($0,a,": "); print a[2]}')
使用solarctl生成虚拟机安装包
name为虚拟机上的应用设置一个app名称namespacenamespacecluster集群
solarctl workload entry configure --app <app> --wgnamespace <namespace> --clusterID <cluster> --network $NETWORK -o solarmesh-vm
执行命令之后,solarctl会生成一个包含所有文件的安装包solarmesh-vm.tar.gz
$ solarctl workload entry configure --app demo --wgnamespace vm --clusterID cluster01 --network $NETWORK -o solarmesh-vm
buildVersion = 805c9d8067c5a47f56d670ec9aa7c80395cadda7-dirty, buildGitRevision = 805c9d8067c5a47f56d670ec9aa7c80395cadda7-dirty, buildStatus = Modified, buildTag = 805c9d8067c5a47f56d670ec9aa7c80395cadda7-dirty, buildHub = docker.io/istio
warning: a security token for namespace vm and service account default has been generated and stored at solarmesh-vm/istio-token
2021-08-25T05:31:20.883847Z info Downloaded a file istio-sidecar.rpm with size 38485057
2021-08-25T05:31:45.377529Z info Downloaded a file istio-sidecar.deb with size 38816702
2021-08-25T05:31:45.832971Z info Downloaded a file ubuntu-setup.sh with size 13
2021-08-25T05:31:45.865458Z info Downloaded a file configure.sh with size 13
2021-08-25T05:31:45.899157Z info Downloaded a file centos-setup.sh with size 13
configuration generation into directory solarmesh-vm was successful
$ ls
solarmesh-vm solarmesh-vm.tar.gz
接管虚拟机 #
将安装包复制到虚拟机中,解压缩
tar xvf solarmesh-vm.tar.gz
cd solarmesh-vm
先检查环境
$ ./configure.sh
os: CentOS
Success
Please use centos-setup.sh
若环境不符合要求可以参考
参考/故障排除
环境监测正常之后,即可执行安装脚本
ubuntu系统可执行ubuntu-setup.sh
$ ./centos-setup.sh
istio started
看到脚本输出istio started,说明已经启动成功了
查看istio的日志,如果看到类似于以下输出,说明虚拟机已经被成功接入
$ cat /var/log/istio/istio.log
2021-09-06T08:05:26.328238Z info FLAG: --concurrency="0"
2021-09-06T08:05:26.328449Z info FLAG: --domain=""
2021-09-06T08:05:26.328542Z info FLAG: --help="false"
2021-09-06T08:05:26.328582Z info FLAG: --log_as_json="false"
2021-09-06T08:05:26.328633Z info FLAG: --log_caller=""
2021-09-06T08:05:26.328665Z info FLAG: --log_output_level="default:info"
2021-09-06T08:05:26.328691Z info FLAG: --log_rotate=""
2021-09-06T08:05:26.328718Z info FLAG: --log_rotate_max_age="30"
2021-09-06T08:05:26.328744Z info FLAG: --log_rotate_max_backups="1000"
2021-09-06T08:05:26.328773Z info FLAG: --log_rotate_max_size="104857600"
2021-09-06T08:05:26.328799Z info FLAG: --log_stacktrace_level="default:none"
2021-09-06T08:05:26.328858Z info FLAG: --log_target="[stdout]"
2021-09-06T08:05:26.328881Z info FLAG: --meshConfig="./etc/istio/config/mesh"
2021-09-06T08:05:26.328894Z info FLAG: --outlierLogPath=""
2021-09-06T08:05:26.328907Z info FLAG: --proxyComponentLogLevel="misc:error"
2021-09-06T08:05:26.328919Z info FLAG: --proxyLogLevel="warning"
2021-09-06T08:05:26.328932Z info FLAG: --serviceCluster="istio-proxy"
2021-09-06T08:05:26.328944Z info FLAG: --stsPort="0"
2021-09-06T08:05:26.328956Z info FLAG: --templateFile=""
2021-09-06T08:05:26.328970Z info FLAG: --tokenManagerPlugin="GoogleTokenExchange"
2021-09-06T08:05:26.328989Z info Version 1.9.4-13fb8ac89420d8cc5b3f895adc614233e805a61c-Clean
2021-09-06T08:05:26.331302Z info Apply mesh config from file defaultConfig:
proxyMetadata:
CANONICAL_REVISION: latest
CANONICAL_SERVICE: gateway
ISTIO_META_CLUSTER_ID: cluster06
ISTIO_META_DNS_CAPTURE: "true"
ISTIO_META_MESH_ID: ""
ISTIO_META_NETWORK: network6
ISTIO_META_WORKLOAD_NAME: gateway
ISTIO_METAJSON_LABELS: '{"app":"gateway","service.istio.io/canonical-name":"gateway","service.istio.io/canonical-version":"latest"}'
POD_NAMESPACE: mall
SERVICE_ACCOUNT: default
TRUST_DOMAIN: ""
2021-09-06T08:05:26.336046Z info Apply proxy config from env
serviceCluster: gateway.mall
controlPlaneAuthPolicy: MUTUAL_TLS
discoveryAddress: istiod.istio-system.svc:15012
2021-09-06T08:05:26.338443Z info Effective config: binaryPath: /usr/local/bin/envoy
concurrency: 2
configPath: ./etc/istio/proxy
controlPlaneAuthPolicy: MUTUAL_TLS
discoveryAddress: istiod.istio-system.svc:15012
drainDuration: 45s
parentShutdownDuration: 60s
proxyAdminPort: 15000
proxyMetadata:
CANONICAL_REVISION: latest
CANONICAL_SERVICE: gateway
ISTIO_META_CLUSTER_ID: cluster06
ISTIO_META_DNS_CAPTURE: "true"
ISTIO_META_MESH_ID: ""
ISTIO_META_NETWORK: network6
ISTIO_META_WORKLOAD_NAME: gateway
ISTIO_METAJSON_LABELS: '{"app":"gateway","service.istio.io/canonical-name":"gateway","service.istio.io/canonical-version":"latest"}'
POD_NAMESPACE: mall
SERVICE_ACCOUNT: default
TRUST_DOMAIN: ""
serviceCluster: istio-proxy
statNameLength: 189
statusPort: 15020
terminationDrainDuration: 5s
tracing:
zipkin:
address: zipkin.istio-system:9411
2021-09-06T08:05:26.338520Z info Proxy role ips=[10.10.13.112 fe80::250:56ff:feb2:c6f9 172.17.0.1 fe80::42:72ff:fec0:cf] type=sidecar id=localhost.mall domain=mall.svc.cluster.local
2021-09-06T08:05:26.338576Z info JWT policy is third-party-jwt
2021-09-06T08:05:26.338612Z info Pilot SAN: [istiod.istio-system.svc]
2021-09-06T08:05:26.338652Z info CA Endpoint istiod.istio-system.svc:15012, provider Citadel
2021-09-06T08:05:26.338809Z info Using CA istiod.istio-system.svc:15012 cert with certs: /etc/certs/root-cert.pem
2021-09-06T08:05:26.339299Z info citadelclient Citadel client using custom root cert: istiod.istio-system.svc:15012
2021-09-06T08:05:26.451797Z info ads All caches have been synced up in 134.652588ms, marking server ready
2021-09-06T08:05:26.453784Z info sds SDS server for workload certificates started, listening on "./etc/istio/proxy/SDS"
2021-09-06T08:05:26.453912Z info sds Start SDS grpc server
2021-09-06T08:05:26.455366Z info xdsproxy Initializing with upstream address "istiod.istio-system.svc:15012" and cluster "cluster06"
2021-09-06T08:05:26.455415Z info dns Starting local udp DNS server at localhost:15053
2021-09-06T08:05:26.455478Z info dns Starting local tcp DNS server at localhost:15053
2021-09-06T08:05:26.456105Z info Starting proxy agent
2021-09-06T08:05:26.456202Z info Opening status port 15020
2021-09-06T08:05:26.456321Z info Received new config, creating new Envoy epoch 0
2021-09-06T08:05:26.456442Z info Epoch 0 starting
2021-09-06T08:05:26.505108Z info Envoy command: [-c etc/istio/proxy/envoy-rev0.json --restart-epoch 0 --drain-time-s 45 --parent-shutdown-time-s 60 --service-cluster istio-proxy --service-node sidecar~10.10.13.112~localhost.mall~mall.svc.cluster.local --local-address-ip-version v4 --bootstrap-version 3 --log-format %Y-%m-%dT%T.%fZ %l envoy %n %v -l warning --component-log-level misc:error --concurrency 2]
2021-09-06T08:05:26.821340Z info cache Root cert has changed, start rotating root cert
2021-09-06T08:05:26.821615Z info ads XDS: Incremental Pushing:0 ConnectedEndpoints:0 Version:
2021-09-06T08:05:26.821741Z info cache generated new workload certificate latency=368.906025ms ttl=23h59m59.178290471s
2021-09-06T08:05:26.863366Z info xdsproxy connected to upstream XDS server: istiod.istio-system.svc:15012
2021-09-06T08:05:27.045938Z info ads ADS: new connection for node:sidecar~10.10.13.112~localhost.mall~mall.svc.cluster.local-1
2021-09-06T08:05:27.045937Z info ads ADS: new connection for node:sidecar~10.10.13.112~localhost.mall~mall.svc.cluster.local-2
2021-09-06T08:05:27.046418Z info cache returned workload certificate from cache ttl=23h59m58.953609867s
2021-09-06T08:05:27.047955Z info sds SDS: PUSH resource=ROOTCA
2021-09-06T08:05:27.049474Z info sds SDS: PUSH resource=default
如果虚拟机已经被成功接入,就意味着虚拟机已经成为了集群的一部分,在虚拟机上可以通过service地址访问集群中的其他服务
声明虚拟机应用 #
在接入虚拟机之后,我们需要声明虚拟机上运行的应用,让集群内的服务可以访问到虚拟机上的应用
在SolarMesh的页面上创建一个ServiceEntry指向虚拟机上的一个应用,hosts配置访问虚拟机应用的域名,endpoints配置虚拟机的ip,ports配置虚拟机上应用的端口,类似于下图所示
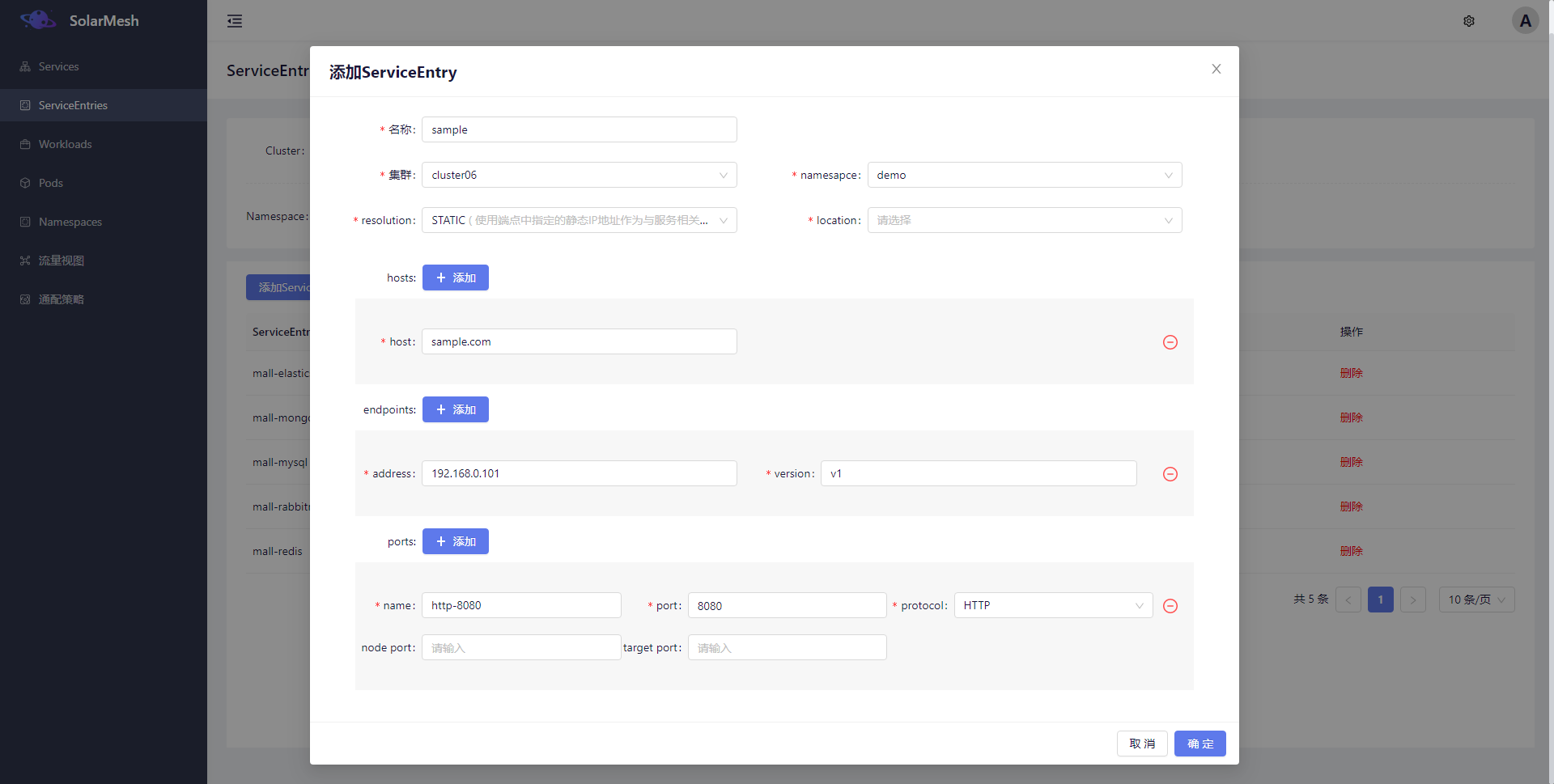
访问虚拟机应用 #
当ServiceEntry创建成功,集群内的服务就可以通过hosts去访问虚拟机应用了
⚠️在访问之前记得关闭虚拟机上的防火墙,或者在防火墙上打开应用相应的端口,让请求可以顺利访问进去
下图是部署在solarmesh中的一个电商项目mall-swarm的流量视图,其中基础设施mysql,redis,mongodb部署在虚拟机中,业务服务部署在集群中